Individuals, small businesses, or big corporations — no one is 100% safe from cybercrimes.
According to the FBI’s Internet crime records, the security of nearly 33 billion accounts was compromised last year. This means there have been 97 cybercrime victims every hour.
The intensity of these crimes can range from using your personal information for illegal activities to breaking into your home. Hackers can also steal your money or create new accounts on your behalf.
For this reason, it’s essential to regularly check if your accounts are secure and Have I Been Pwned? (HIBP) is a tool that can help you with just that.
Let’s see how this tool helps with account security, how to use it, and why must you use this free tool evenif you’ve entrusted some big company with your data security needs.
Let’s get started!
What Does ‘Pwned’ Mean?
Pwned means defeated. It sprouted from the world of computer gaming and hacking and originated as a typographical error in the word ‘owned’. Over time, this error gained popularity and transformed into a deliberate variation.
The word indicates dominance or victory over an opponent in the gaming and hacking subcultures. So when a player or system is said to be “pwned,” it means that they have been thoroughly defeated, controlled, or compromised by another player or hacker. The term is often employed in a lighthearted or mocking manner to emphasize the extent of the victory.
Outside of gaming and hacking contexts, “pwned” is used more broadly to convey the idea of being defeated or outsmarted in security-related situations.
What Is ‘Have I Been Pwned’ (HIBP)?
HIBP is an online tool that allows you to check whether your account is compromised or not. It was developed in 2013 by Troy Hunt, an Australian security researcher who collected millions of pwned accounts from hundreds of breaches.
As of today, the HIBP official website reports to have collected 12,868,997,436 pwned accounts with 740 pwned websites. This collection includes:
- 268,765,495 Wattpad accounts
- 509,458,528 Facebook accounts
- 359,420,698 Myspace accounts
For someone completely new to the tool, Troy and his team have provided a detailed breakdown of all important terms on their FAQ page and it’s a good idea to check it out.
However, you’ll need to know the following to understand this post further:
1. Data Breach
The HIBP website defines a data breach as:
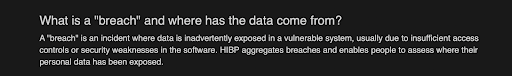
In simpler words, a breach is when any of your private information (like passwords, security pins, or addresses) gets revealed to others.
2. Paste
HIBP defines a “paste” as:
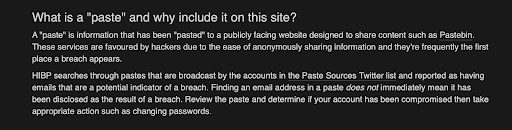
In simple words, a “paste” is compromised information shared on public websites (such as Pastebin). HIBP checks these pastes for emails linked to potential breaches, helping you know if your info was shared without permission
How Does HIBP Work?
To use HIBP, you can go to the website and enter your email address in the search bar:
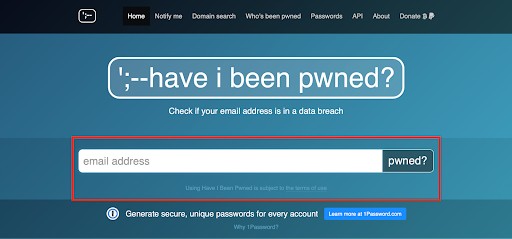
Press enter and the tool will analyze all the data associated with your email address and display its security status. There are two possible results:
1. Your account is safe. In this case, you’ll see:
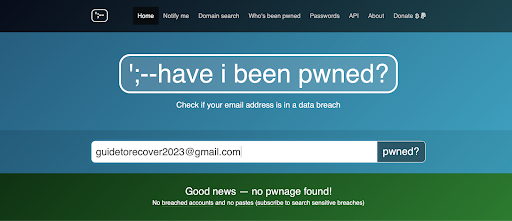
2. You’ve been pwned, in which case you’ll see:
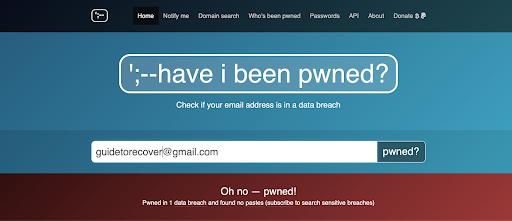
If you wish to check the security status of all email addresses associated with your domain, you can use the domain search feature.
In both cases, HIBP cross-checks your data against all the public sources that broadcast breached data. The tool also checks information against publicly shared snippets and pastes.
What to Do if You Have Been Pwned?
If you have been pwned, the first recommended step is to change your password. HIBP recommends using 1Password to do so — but you can do it manually too. Here are some best practices for setting up a strong, secure password:
- Use super-long passwords (phrases or even sentences)
- Use acronyms, digits, and special characters in between the letters
- Use a unique password for each online account.
- Do not use a variation of your old password
Secondly, enable two-factor or multi-factor authentication. When signing in, this will require you to present multiple pieces of evidence of your identity before granting access to your account. This means even if someone has the first piece of the puzzle figured out — which is your password — they won’t be able to break into your account.
4 Tips to Keep Your Account Secure
If you haven’t been pwned yet, that’s great! But we highly recommend taking these measures to fully secure your account:
1. Check the Accounts Associated With Your Email Address
If you frequently use Gmail to sign up online, use an email cleaner like Mine to identify all the accounts linked to your email address. By removing any inactive accounts, you minimize potential points of vulnerability and reduce the risk of unauthorized access.
Advanced email cleaners also employ algorithms to detect suspicious patterns and activities within your inbox. They can identify phishing attempts, unauthorized login attempts, and other malicious activities. This provides an additional layer of defense against potential security threats.
2. Clear Junk Emails
Junk emails can be a breeding ground for phishing attacks and malware. Routinely clear out your spam and junk folders to minimize the chances of falling victim to malicious schemes.
You also want to avoid clicking on suspicious links or downloading attachments from unknown sources. This reduces the likelihood of encountering harmful content that could compromise your account security.
3. Update Your Apps and Devices
Developers release updates to patch vulnerabilities and enhance security features. Ignoring these updates leaves your systems exposed to exploitation.
You want to enable automatic updates whenever possible and manually check for updates if automation is not available. This simple yet effective practice ensures that you benefit from the latest security measures.
4. Monitor Your Accounts Closely
Finally, stay vigilant by keeping a close eye on your account activity. Most online platforms provide features that allow you to review recent logins, device access, and login locations.
Regularly check these logs to ensure there are no unauthorized access points. If you spot any unfamiliar devices or locations, take immediate action, such as changing your password and reviewing security settings.
Track emails, email reminders & templates in Gmail for free
Upgrade Gmail with the features it’s missing
Add to GmailDavid Campbell
David Campbell is the editor of the Right Inbox blog. He is passionate about email productivity and getting more done in less time.